Illustration: Hit&Run
Globalization is a memory, disruption yesterday’s buzzword. Today’s must-embrace business strategy for global corporations is digital transformation.
Banks from Halifax to Hanoi are full of teams from Accenture and McKinsey desperately trying to wring modernity from legacy systems and embed ‘Agile’ into ‘DevOps’ with walls of Post-It notes and weeks of PowerPoints. Bright young things, hired on the basis of a stint at Google, are re-badged ‘head of digital’, given multi-million-dollar budgets and the power to boss the business.

|
Digital transformation means giving employees and clients what they want. And they want multichannel, multi-device access, mobile and bring-your-own-device (BYOD) connectivity, instant payments, instant access to personal data and products tailored on the fly to their personal or corporate requirements.
Half-kidding aside, the management and market obsession with transformation is not all good news. There are problems here, and the biggest of them by far is a fundamental outcome of the whole process that gets worse the better banks (and business in general) are at going digital.
It means re-engineering the entire suite of retail and wholesale banking products so that they can be delivered over digital channels, bundled with advanced analytics and plugged into a huge and increasing array of bank and non-bank platforms. It also means digitalizing the thousands of dull, manual, administrative tasks in legal, HR, procurement and a dozen other departments, applying new techniques like robotic process automation. And that is before even thinking about AI, AR and blockchain and all the other emerging technologies.
With all of that comes efficiency and innovation and opportunity.
And an explosion of cyber-risk.
Because the race to digitalize is a race to exponentially increase your attack surface – the number of points at which cyber criminals can gain entry to your systems and do you harm.
What really concerns me is the sophistication of the capability, which is becoming good enough to really threaten parts of our critical infrastructure, certainly in the financial, banking sector – Rob Wainwright, Europol
This is the battlefield on which the banks find themselves today. An asymmetric theatre of war in which it costs almost nothing to attack and cripple a bank but in which it costs billions to defend; where an attacker has to be lucky once, but the defence has to be lucky every time; a battlefield in which the adversaries can range from a teenage vandal to a military cyber ops team and where off-the-shelf weapons come complete with comprehensive customer service.
The digital overhaul of retail and wholesale banking, although long overdue, is rapidly expanding this battlefield in both size and complexity. Add the fragilities and complex dependencies of one-off integrations between legacy and newer systems, the hyper-connectivity of the internet of things (IoT), the impossibility of ensuring the security of third-parties and the industrialization of fraud and other cybercrime that digitization enables, and it is clear that digital transformation does not simply entail the usual commercial and competitive risks of a big strategy initiative. It contains a potentially existential threat to even the largest and strongest institutions.
For banks, already the biggest targets in cyberspace, digital transformation may be the ultimate test of Nietzsche’s maxim: “That which does not kill us, makes us stronger.”
Prime targets
Banks are prime targets in cyberspace for the same reason that they have always been targets – the money. Smart criminals have long since abandoned guns and dynamite as their tools of choice and now steal billions via direct cyberattacks on financial infrastructure or through fraud on banks’ retail and wholesale customers.
Just how lucrative these attacks can be was emphasized at the end of March this year, when the alleged mastermind behind the so-called Carbanak/Cobalt cyberheist was finally arrested in Alicante, Spain, after a three-year investigation conducted by the Spanish National Police, with the support of Europol, the US Federal Bureau of Investigation (FBI), the Romanian, Moldovan, Belarussian and Taiwanese authorities and private cybersecurity companies. Spain’s interior ministry named the suspect only as Denis K, a Ukrainian national.
According to Europol: “Since 2013, the cybercrime gang have attempted to attack banks, e-payment systems and financial institutions using pieces of malware they designed, known as Carbanak and Cobalt. The criminal operation has struck banks in more than 40 countries and has resulted in cumulative losses of over €1 billion for the financial industry. The magnitude of the losses is significant: the Cobalt malware alone allowed criminals to steal up to €10 million per heist.” Try stealing more than $1 billion using conventional bank robbery.
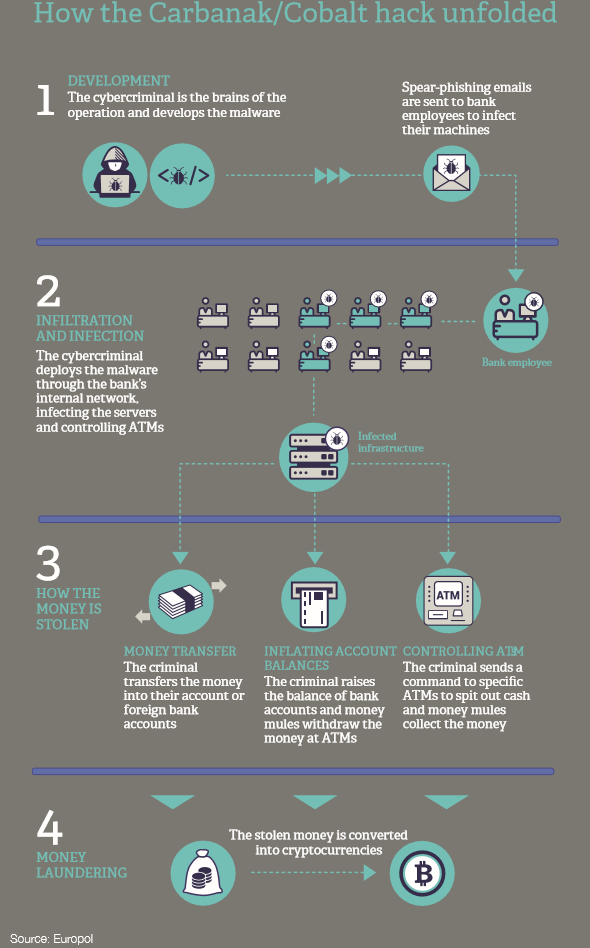
Carbanak was particularly large, but digital criminals attacking for profit is the bread and butter of cyberactivity against the banks. A new, and potentially much more serious, development is the entry of cash-strapped nation state threat actors whose motivations are also financial.
“Directly stealing money out of bank accounts is something that has not traditionally been the purview of nation states,” Jon Condra, director of east Asian research and analysis at the threat intelligence firm Flashpoint, commented earlier this year. “This has been an interesting twist in the APT [advanced persistent threat] saga coming out of the east Asian region.”
“East Asian” is poorly disguised code for Team America’s favourite rogue state, and in October 2017 it struck again. Taiwan’s Far Eastern International Bank announced that cybercrooks had planted malware on its systems, gained access to its Swift terminal and wired $60 million to banks in the US, Cambodia and Sri Lanka. According to BAE Systems researchers and others, the cyberattack, bore “some of the hallmarks” of Lazarus, a hacking group linked to North Korea and to the notorious 2016 Bangladesh central bank heist in which over $80 million was stolen.
In December 2017, the US and UK governments explicitly blamed North Korea for the WannaCry ransomware attack that hit more than 300,000 computers in 150 countries, causing billions of dollars of damage, including inflicting serious damage on the UK’s National Health Service. If the attribution is correct, a nation state used a hack (Eternal Blue) covertly developed and then lost by a government (the US National Security Agency) and then leaked by a group allegedly linked to the Russian state (the Shadow Brokers) to extract money and circumvent sanctions by blackmailing businesses all over the world with the encryption of their own data, charging a ransom to decrypt it again.

Tom Bossert, homeland security adviser to president Donald Trump, holds a press briefing to publicly blame North Korea for unleashing the so-called WannaCry cyber attack
This kind of attack worries the banks more than simpler types of fraud because of the sophistication of the hacking techniques that nation states can afford to develop and deploy, and because private companies are in a poor position to fight such adversaries.
“Nation states desperate for cash are now stealing money from financial institutions,” says the chief security officer at one of the world’s largest global banks. “That scares me and it’s real. WannaCry included nation-state tools built by super-secret organizations in developed countries.”
Most nation states have better hackers than private companies have defences. Add in the fact that truly powerful organizations like the US National Security Agency (NSA) are losing control of their cyberweapons, and the problem just got a lot worse.
Large financial institutions are also targets because they are proxies for countries and governments. In cybersecurity lingo they are critical national infrastructure (CNI) – systemically important entities whose disruption could materially damage a country or at the very least cause embarrassment or irritation. The growing upswell of hostile cyberactivity that has accompanied what the UN has declared a renewal of the Cold War has CNI firmly in its sights.
This includes the continuing series of cyberattacks on Ukraine’s infrastructure from 2015 onwards; the 2016 indictment of seven Iranians in the US for their roles in cyberattacks on a dam and DDoS (distributed denial-of-service) attacks on a number of banks; the Russian ‘Cozy Bear’ involvement in the US elections revealed by Dutch intelligence; the cyberattacks on the French elections; and the March 2018 Russian cyberattacks on the German government that have been called “a form of warfare” by one German MP.
But it also puts the big banks on the frontline of this new war. Disabling a prominent financial organization is a high-profile way to embarrass a government. Disrupting the data flow between institutions can cause volatility in key markets and unsettle the public. And a full-scale attack on, say, the ATM system could cause panic and provoke uncontrolled bank runs.
“We are also now a CNI target – we are a nation-state target, and so the threat landscape has become much more complex,” says one global bank’s chief information security officer (CISO).
“If you want to embarrass a head of state or a security service or a country as a whole, then what better way than to take down that country’s largest or most high-profile bank, just for laughs?” says another. “And what ability does any private-sector organization really have to prevent that kind of attack if the adversary is really committed to it?”
These fears also have law enforcement and regulators on high alert.
“What really concerns me is the sophistication of the capability, which is becoming good enough to really threaten parts of our critical infrastructure, certainly in the financial, banking sector,” says Rob Wainwright, the outgoing director of Europol, the EU’s law enforcement intelligence agency.

Rob Wainwright, the outgoing director of Europol
In the US, cybersecurity is the top priority for the Treasury department’s Office of the Comptroller of the Currency, according to its newly released bank supervision operating plan for 2018. This follows on from comments Comptroller of the Currency Keith Noreika had already highlighted in an OCC Risk Perspective earlier this year: “Cyber threats are increasing in speed and sophistication. These threats target large quantities of personally identifiable information and proprietary intellectual property and facilitate misappropriation of funds at the retail and wholesale level.”
The April 16 joint statement from the Department of Homeland Security (DoHS), the FBI and the UK’s National Cyber Security Centre (NCSC) on malicious cyber activity carried out by the Russian government is just the latest reminder of the nation state threat.
And while banks’ new generation of cybersecurity chiefs are trying to harden their systems to cope with ever-smarter organized crime and nation-state attacks, the script kiddies have not gone away. The old cliché of the teenage hacker wreaking havoc from their bedroom is now outdated. But it is not completely obsolete.
In January this year, Dutch banks ABN Amro and ING were hit by DDoS attacks that took their mobile and online banking services offline for several hours. Just as systems were coming back online, a new wave of attacks struck, this time also hitting other banks such as Rabobank, the Dutch tax authority and DigiD, the country’s login system for governmental services. The attacks on both the banks and institutions continued for almost a week. To emphasize how routine this kind of thing has become, Dutch central bank (DNB) president Klaas Knot revealed that his institution faced similar attacks at the rate of roughly one a second.

Dutch central bank president Klaas Knot
At first Russian involvement was suspected, because the attacks came shortly after the publication of the fact that the Dutch intelligence agency, AIVD, had provided the crucial intel linking Russia’s Cozy Bear group to the Russian government and the US Democratic party email hack.
But it quickly became clear that a local 18-year-old, Jelle S, who had already been caught DDoS-ing a smaller Dutch bank, Bunq, had admitted the later attacks. He claimed his motivation was: “To see everybody freak out and blame Russia while you know you did it – that’s funny.”
In an illustration of how easy it is to execute this type of attack, Jelle S claimed to have bought a ready-made ‘stresser’ DDoS package on the dark web, for which he had paid €50 a week, to launch attacks with a volume of about 40 gigabits per second (Gbps). Stresser services are websites that offer DDoS capability as a paid service.
As McAfee’s chief scientist, Raj Samani, comments: “You can disrupt your competition for the price of a cup of coffee.” (To give an idea of the scale of this attack, which brought down some banks for several hours, the two largest DDoS attacks seen recently, against GitHub and an unnamed US company protected by Arbor Networks, delivered 1.3 terabits per second (Tbps) and 1.7Tbps respectively – more than 30 times bigger).
One final reason that the banks are so frequently attacked by such a wide range of hackers is precisely because they are so well defended. As Mike Hulett, head of operations at the NCA’s National Cyber Crime Unit, explains: “The banks are obviously attacked for financial reasons, but actually a lot of the time it is because they are the best defended – so attackers use them as a test bed. If something works – or partly works – against the banks, then it will probably work against the worst defended.”
Hostile environment
So the banks are targets for everyone from bored teenagers to hard-up dictators and the environment is getting more and more hostile. But banks are not simply vulnerable because everyone wants to attack them. Their size and their unique function also give attackers an almost infinite number of ways in.
Leaving DDoS attacks aside, because they are designed to disrupt a target’s digital footprint not steal data or hide inside it, by far the easiest way for a cybercriminal to attack and penetrate a target organization is through malware-infected email. In the jargon, this is overwhelmingly the most common attack vector. And with good reason.
There is hardware, there is software and then there is wetware – you and I. And we are the weakest link in the cybersecurity chain because we can be tricked relatively easily into opening emails and clicking on attached documents or images that contain code that then download malware onto our device.
What that malware does next depends on its authors’ objectives, but cybercriminals are largely economically motivated and the easiest ways to monetize a successful breach are to encrypt valuable data and demand cash to make it usable again (ransomware) or to explore the network in the search for data that can be exfiltrated and sold elsewhere.
This can be personal data that can be used to compromise other websites or gain access to credit cards or bank accounts, or it can be commercially sensitive or market-moving data.
This kind of cyberattack is called phishing and anyone with an email account is vulnerable. Large organizations with thousands of employees connected 24/7 on global networks, increasingly via mobile and BYOD, are therefore especially at risk.
“Yes, people are a big risk,” says Christian Bluhm, group risk officer at UBS. “And that means that training and awareness are critical. We regularly test people on phishing and we have anti-phishing functionality built into people’s email application. It also means that HR is a key point of contact and critical in securing the organization.”
There are only two types of companies: those that have been hacked and those that will be. And even they are converging into one category: companies that have been hacked and will be hacked again – Robert Mueller, former director of the FBI
This training needs to be continuous because phishing is getting really clever. Carbanak was a sophisticated attack that attacked bank infrastructure using a complicated combination of attack methods, malware and monetization techniques to achieve its goals.
But it was only possible because bank employees were targeted by spear-phishing emails. These are emails ostensibly from a trusted sender, often containing information already stolen from the recipient’s mailbox or those of their contacts to tailor the lure to a real recent task or transaction, which can be extremely difficult to distinguish from genuine communications. In the case of Carbanak, it was this type of sophisticated email that tricked employees into giving the attackers the access to internal systems they needed.
Even cleverer are the email frauds that do not even require a technical exploit. Business email compromise (BEC) frauds involve emails purporting to come from senior management, typically the chief executive or chief financial officer, sent to more junior finance staff with instructions to make large payments from the business in connection with alleged M&A or other activity. The fraudsters often spend months inside corporate systems researching companies’ emails, the writing style of executives, details of financial procedures and suppliers and any information they can include to make the emails seem authentic.
It is amazingly effective. In January 2016, Austrian aeronautical engineering firm FACC admitted that it had lost up to €50 million when someone impersonating the chief executive in an email had authorized the transfer of funds. The CEO and CFO were fired and a man arrested in Hong Kong for money laundering. Unusually, most of the money was recovered. In the same year, Leoni, a leading wire and cable manufacturer, lost €40 million to a similar scam.
Globally, in 2018 it is estimated that BEC fraud will cost business $9 billion, according to security provider Trend Micro, extrapolating from FBI data.
“Cybercriminals and threat actors take advantage of existing platforms and technologies when launching their attacks, so as new ones emerge and go mainstream, these criminals will follow suit and improve their arsenal,” said Trend Micro’s security focus lead, Paul Joseph Oliveria, when launching the report last December, emphasizing that banks’ rush to digital transformation was a boon for the cybercriminals.
Hackers, particularly quasi-state entities, are also getting more sophisticated in their commercial espionage.
“We find analysts deep in the organization [that is, not easy to find in the public domain] being targeted because they are working on a particular project or a team working on a specific deal. This tells us we have a very specific adversary looking to obtain very specific IP [intellectual property]. That’s what makes it different today,” says one US bank CISO.
Reputational damage
Banks’ vulnerability to human error extends beyond employees to their customers. Of course, most businesses fear losing customer data. As breaches from TalkTalk to Yahoo to Equifax have shown, the reputational damage is huge, M&A deals can be repriced down by large percentages and senior management can lose both money and their jobs.
Banks themselves have lost customer data through breaches – in 2014, a cyberattack on JPMorgan compromised data associated with over 83 million accounts. More recently, in July 2017, UniCredit revealed a data breach affecting 400,000 customers. And for some, such as wealth management institutions, loss of client data is an existential threat.
“We have established a clear set of risk taxonomies – a clear hierarchy of things to be protected – and client PID [personal identification] is an absolute priority,” explains one head of security at a large private bank. “We have identified that the greatest damage that a cybersecurity incident could do to the bank would be via a client data theft. Imagine if the details of the top 50 ultra-high net-worth individuals were leaked – that would be one of our disaster scenarios and not simply because of banking secrecy laws and the penalties there. So a key objective is that data. It’s a line in the sand. And of course, that kind of data can be got by phishing our clients as well as by attacking us. And so we run many exercises around that.”
But banks’ customer-related cybersecurity liabilities stretch far beyond the loss of personal information that all companies fear. First, almost every digital interaction between a customer and a bank exposes that customer’s most valuable data and opens a potential door to their money. Securing that connection without making digital banking so difficult people find another supplier is a critical business issue.
Paul Gillen, interim group information security officer at Barclays, is emphatic: “Customers, clients and investors expect us to deliver industry-leading, personalised services to them quickly and they hold us accountable for security. Barclays takes cyber security extremely seriously and we continue to invest in the people, processes and technology to keep the systems safe and allow for an uninturrupted customer experience.”
More than that, few companies are under such pressure to pay for their customers’ mistakes or misfortunes, regardless of a legal responsibility to do so. Look at the recent outcry over the refusal of the UK operations of Santander to cover the costs of so-called transfer fraud, in which victims, often in the middle of house purchases, are tricked by email into transferring cash into fraudsters’ bank accounts. In the UK alone, almost £101 million was stolen between January and June last year through this type of attack. Because these transfers are made by account holders using their correct identity and authentication data, the banks are not legally responsible.
However, some banks, including Spain’s CaixaBank, have realized that the reputational issues of sticking to the letter of the law are so large that they refund customers who have been tricked in this way regardless. And in November 2017 the UK Financial Conduct Authority (FCA) and the Payment Systems Regulator announced that they would be looking at ways to ensure customers were reimbursed.
This additional complexity of protecting customers from themselves, as well as ensuring that bank connectivity is secure, on top of the need to secure employees and their technology, creates a huge cybersecurity problem.
It is not just about people. As Carbanak showed, compromising outward-facing bank technology can create big losses for the banks and profits for the cybercriminals.
“One of our key objectives is operational resilience. Imagine if our ATM network was taken down – again that would be a disaster,” says one CISO.
Investment banks don’t have millions of consumer customers, but they are still vulnerable.
“We’re not a high-street bank, so we are very rarely pulled into the kinds of attacks that commonly hit them and that you read about: so we do not generally get hit by those DDoS attacks or ransomware unless we are just collateral damage like Maersk and Merck were in notPetya,” explains the deputy CISO of a large investment bank.

(The world’s biggest shipping company AP Moller-Maersk put the cost of a cyberattack last year at up to $300 million; pharma giant Merck lost up to $275 million in the same attack; both were victims of the notPetya pseudo-ransomware virus that the US and UK announced in February this year was launched by Russia to disrupt Ukrainian infrastructure and then ‘escaped’ its primary theatre.)
The deputy CISO continues: “Instead we get targeted by the more sophisticated attackers who are interested in specific information on an IPO or an M&A deal. So we are more likely to experience industrial or state espionage via malware and via APTs.”
And, as Michael Colao, CISO of Axa UK says, the criminals are having to evolve away from easy phishing expeditions, “because big corporations like banks tend not to pay. They have sophisticated backups and their ransoms would be large and easy to trace. So criminals are devising smarter and smarter ways to try to extort them. One is a so-called integrity attack. ‘We have changed 850 words and numbers in your systems. We won’t tell you where or what. Might be in spreadsheets or prospectuses or smart contracts. Pay up or those changes may do untold damage at some point.’”
And all the banks face almost unsolvable problems of malicious insiders – employees with privileged access who want to do damage – and third parties in their supply chains.
New gateways
Digital transformation is the gasoline for this fire. In retail banking, for the larger banks, it means moving to a mobile banking model in which customers use an app to do everything from make payments to compare mortgage options. The endgame here is products such as Imaginbank from unlikely digital leader CaixaBank, a mobile-only (no desktop version) offering, complete with Facebook-accessed chatbot and Imaginbank cafés.
The UK’s Monzo (and other so-called challenger banks) similarly allow access only via mobile apps, but, unlike Imaginbank, offer few conventional banking services directly, instead earning commission from connecting their users to other providers, a model which itself creates a greater potential attack surface for the criminals.
It is not just apps. CaixaBank has realized that to improve its sales offering, it must equip its salespeople with connected PCs able to take a client through the entire product sales process, from questionnaire to signed contracts. This creates thousands of new network endpoints, each a potential gateway into the bank’s systems. The bank is well aware of the security implications, but this example is another illustration of how digitization is creating a vast new attack surface on which criminals can operate.
All these initiatives are a ready-made opportunity for cybercriminals to expand their digital robbery palettes. And they are all over banks’ digital offerings as it is.
Anyone who Googles ‘FCA news cloned websites’ (and be careful, the FCA brand itself has been spoofed in phishing campaigns against the UK financial sector) will be presented with a long list of financial institutions whose websites are cloned by attackers trying to trick customers into entering their key authentication details into a fake site, so that the hackers can then access their real accounts and empty them.
All it takes is for a customer to click on an email that appears to come from their bank with a message saying, for example, that their account has been compromised and they need to log on to reactivate it, and the damage is done. Or they may click on a bank logo included on the cloned third-party website of a sporting event that they have sponsored – a website they had no part in developing. And as the list shows, it is not just banks, it is also asset managers like BlackRock and crowdfunders like Funding Circle. For this reason, mobile application management is a full-time job requiring the help of external intelligence providers.
More sophisticated criminals use increasingly clandestine techniques that are harder to detect. Back in the early days of cybercrime, banking Trojans were a key security concern. These are pieces of software masquerading as legitimate applications, which sit on users’ systems, gain administrator privileges and then can delete, modify or copy data. They can create backdoor access into systems, disguise the actions of other pieces of malicious software and take advantage of vulnerabilities in the software running on a PC or phone.
Instant payment means instant fraud – A bank CISO
One of the most famous is Dridex, which made a comeback in 2017, but there are dozens of families of Trojans siphoning off millions of dollars of customer cash. The rise of mobile banking as part of digital transformation is resurrecting old enemies and feeding the rise of new and more dangerous varieties.
In mid 2017, researchers discovered that one of the most dangerous Android banking Trojan families (Svpeng) now incorporated a keylogger. This meant that it could record any data entered on the keypad, including authentication data for banking apps. It also allowed the Trojan to grant itself the permissions required to prevent victims from uninstalling it.
In its Mobile Threat Report for the first quarter of 2018, McAfee identified various threats, including MoqHao, a Trojan that spread via SMS to account holders at one of the big Korean banks. According to the report, 16 million users suffered mobile malware infections in the third quarter of 2017. That is double the number observed by researchers a year earlier.
And new techniques emerge regularly, such as botnet ad fraud, pay-per-download distribution scams and malicious cryptominers.
The regulators are not helping either, as Carles Solé, CISO, CaixaBank explains: “PSD2 is a big issue. It means that we have to offer sensitive customer data to third parties, but how do we know those providers are themselves secure enough to protect it? If they lose our data, then it is highly likely that our reputation will be damaged as much as theirs. Yes, if we supply data to fintechs they have to be certified by some official body, but they also need to put in place at least the same cybersecurity controls as the banks.
“Even if they have cyber insurance to cover the financial risk there is still that residual reputational risk. And no one is asking them the questions we would usually ask of a third-party provider or supplier. People have been worrying about screen-scraping in PSD2, but that is just the tip of the iceberg.”
In retail banking, as digital transformation is rolled out, and the attack surface created by mobile and desktop applications increases, the cybersecurity risk increases as do the resources that must be devoted to fight it.
“As banks try to become platforms, that process creates new threat surfaces. The more we open up APIs [application programming interfaces], the more that exposes us,” says one CISO.
And as McAfee points out: “Mobile malware authors have set their sights firmly on monetization… this is no doubt a response to the explosion in mobile banking and financial applications that we have seen during the last couple of years.”
The same is true of wholesale banking. In payments, FX, transaction banking, trade finance, capital markets and investment banking, the need for more speed, better connectivity, mobile device access, a better user experience and better analytics has led banks to kick-start the development of digital versions of their products and delivery mechanisms. Clients have continued to demand bank-agnostic platforms and have themselves connected to an increasing number of new platforms and fintechs. This new ecosystem of wholesale financial technology is another area ripe for cyberattack.
In payments, banks are joining global automated clearing-house (ACH) platforms such as PayCommerce and Earthport, as well as self-described alternative to Swift, Ripple. The first of these is a consortium of more than 100 banks; Earthport has local bank partners in 65 countries. Ripple, whose blockchain product, RippleNet, is being explored as a payments vehicle for Santander’s mobile apps, for example, is working with more than 100 banks and payment service providers, according to its new global head of banking, former Swift executive, Marjan Delatinne.
Real-time payments
The cyber risks of joining payment networks have been made all too plain by the various hacks of banks and their Swift connections, of which the theft of $81 million from the Bank of Bangladesh is just the largest. These attacks involved the acquisition of genuine Swift authentication credentials, sometimes with hybrid physical/cyber techniques (the use of USB sticks for example), that allowed attackers, possibly insiders, to make transfers that seemed correctly authorized to the counterparties.
Digital transformation will greatly increase the number of systems and platforms operating in the financial system and raises the risk of these very large thefts substantially.
Worse still, the key aims of these digitization projects make cybersecurity more and more difficult. To take just one example pointed out by a bank CISO: “Instant payment means instant fraud.”
If you are a criminal, irrevocable real-time payments are today’s bearer bonds. With no time for fraud staff to manually review transactions, money is moved instantly to banks in countries beyond the jurisdiction of any authorities willing to act against the thieves.
The problem extends to other areas of wholesale markets. In trade finance, banks are digitizing the physical and financial supply chains as well as the information supply chain – while various fintech platforms are solving specific problems, such as supply-chain finance, for specific types of client.
Players like TradeIX have an even bigger vision of connectivity. Using a combination of blockchain, APIs and the cloud (itself a big source of cybersecurity complexity), and in conjunction with other platforms such as R3, SAP and Ariba, TradeIX wants to connect suppliers, buyers, service providers, B2B networks, credit underwriters and financial institutions of all kinds.
There is no suggestion that TradeIX, or any other platform, is ignoring cybersecurity, but it is simply a fact of life that this level of connectivity, the use of open APIs to give participants access to a wide-range of sensitive client and transaction data, the use of SaaS/cloud technology and the need to interface with crumbling legacy systems is a big security challenge.
TradeIX claims that its distributed platform is “the most connected and secured platform for open account trade finance solutions for financial institutions, B2B networks and technology providers.”
That claim cannot be proved or disproved. But aggregating and connecting all these processes and players creates a multitude of new attack points for cybercriminals. And by using a large graphic on its homepage emphasizing that the TIX platform targets the $8 trillion trade finance market, it is ensuring that criminals understand the scale of their opportunity.
The problem extends to anywhere digital transformation is the driver.
On the bond trading floor, you have platforms such as Algomi’s Honeycomb network, a trade-matching network for corporate bonds. Algomi has teamed up with Euronext on Euronext Synapse to “create a new ecosystem [connecting] pools of liquidity and market participants within a new anonymous inter-dealer centralized market place.”
 |
| Robert Mueller, former director of the FBI |
And then there is Overbond, which claims to be the first end-to-end, fully digital bond origination platform that connects all bond market participants together – corporate and government issuers, dealers and fixed-income investors. The plan is to transform primary bond markets into a fully digital marketplace. The company has recently expanded “real-time access to the Overbond Platform to all US corporate issuers and institutional investors by extending key functionality via desktop and mobile applications,” it says.
This kind of claim is music to the ears of the cyberthief. Again, not because the platforms have not taken security into account, although the cybersecurity expertise and resources of fintechs are open to question, but because of the certainty that organizations will be breached.
It is a cliché of cybersecurity, first stated openly by Robert Mueller, former director of the FBI and now special counsel investigating links between Russia and the Trump campaign during the 2016 presidential election, that: “There are only two types of companies: those that have been hacked and those that will be. And even they are converging into one category: companies that have been hacked and will be hacked again.”
It is a point repeated very recently by Ciaran Martin, chief executive of the UK’s NCSC: “Absolute protection is neither possible nor desirable; it’s about having more resilience in the systems we care about the most.”
In other words, everyone will be successfully hacked at some point and most people already have been, whether they know it or not. So businesses racing to convert to digital and to increase connectivity and speed of operation are increasing their cyber-risk regardless.
Amit Yoran, chairman and chief executive of cybersecurity solution provider Tenable, agrees that “digital transformation has created an explosion of new technologies and computer platforms, from cloud to IoT. This requires a modern approach for understanding and reducing cyber-risk.”
The question is, what is that exactly?




